Hello folks! I’m now trying to figure out another thing as part of my migration from windows =p how to authenticate to a website and how to sign a PDF using a smart card digital certificate.
I’ve found out about lots of stuff already, like the Arch Wiki article on Smart Cards, and using Okular to sign PDFs…
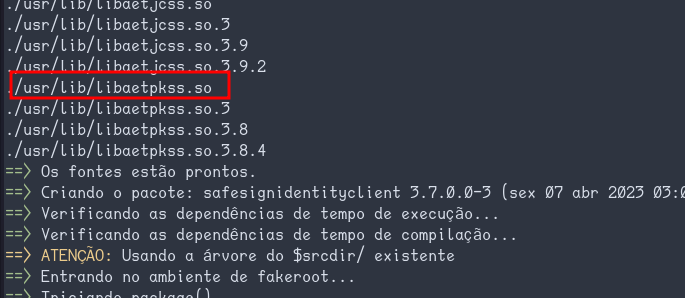
I got around to install the recommended packages with
sudo pacman -S ccid opensc pcsc-tools
sudo systemctl enable pcscd.service
sudo systemctl start pcscd.service
When I run pcsc_scan it properly shows me my reader and details on my card’s certificate:
$ pcsc_scan
PC/SC device scanner
V 1.6.2 (c) 2001-2022, Ludovic Rousseau <ludovic.rousseau@free.fr>
Using reader plug'n play mechanism
Scanning present readers...
0: Gemalto PC Twin Reader 00 00
...
Possibly identified card (using /usr/share/pcsc/smartcard_list.txt):
3B 7D 96 00 00 80 31 80 65 B0 83 11 11 E5 83 00 90 00
3B 7D .. 00 00 80 31 80 65 B0 .. .. .. .. 83 .. 90 00
IDClassic 3XX / Classic TPC (IXS, IS, IS V2, IS CC, IM, IM CC, IM CC V3) / MultiApp ID Cards
3B 7D 96 00 00 80 31 80 65 B0 83 11 11 E5 83 00 90 00
Gemalto TOP DL v2 StdR
eCPF (Cadastro de Pessoas Físicas) from Imprensa Oficial do Brasil
Identidade digital (e-CPF) from Caixa
The Arch Wiki article mentions that
The Chrome, Firefox, Thunderbird and SeaMonkey are automatically processed with pkcs11-register(1) at each login . (Discuss in Talk:Smartcards)
So I shutdown my browser, executed it… and still nothing. Sadly, the “Talk:Smartcards” is completely empty.
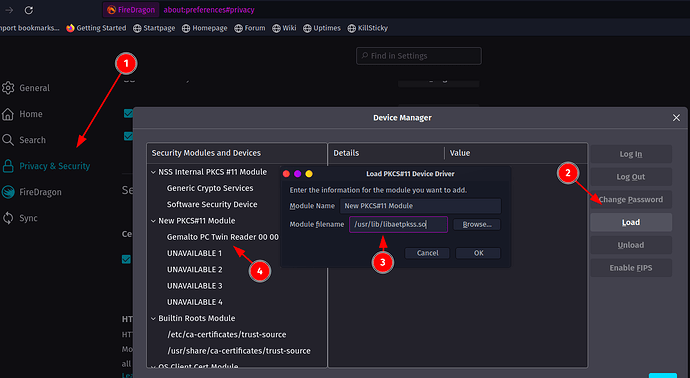
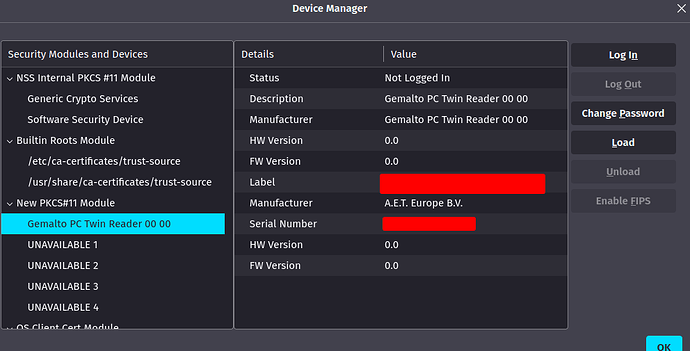
I thought maybe it was enough that pcsc_scan could see my reader and certificate, but I still get no success on trying to login either on FireDragon or Vivaldi, and the certificate also won’t show up on Okular (when I go Tools > Digitally Sign, all I get is an error message about there being no signing certificates available and a link to a manual about adding digital signatures which must be outdated, since there’s nothing about the subject there)
$ garuda-inxi
System:
Kernel: 6.2.9-zen1-1-zen arch: x86_64 bits: 64 compiler: gcc v: 12.2.1
parameters: BOOT_IMAGE=/@/boot/vmlinuz-linux-zen
root=UUID=468e3250-834f-4678-85b1-f50f268e557d rw rootflags=subvol=@
quiet quiet splash rd.udev.log_priority=3 vt.global_cursor_default=0
resume=UUID=92d5bc58-440e-4eab-9f01-4fa35d34e02b loglevel=3 ibt=off
Desktop: KDE Plasma v: 5.27.3 tk: Qt v: 5.15.8 wm: kwin_x11 vt: 1 dm: SDDM
Distro: Garuda Linux base: Arch Linux
Machine:
Type: Laptop System: Dell product: G5 5590 v: N/A
serial: <superuser required> Chassis: type: 10 serial: <superuser required>
Mobo: Dell model: 0F3T2G v: A00 serial: <superuser required> UEFI: Dell
v: 1.22.0 date: 11/10/2022
Battery:
ID-1: BAT0 charge: 48.6 Wh (100.0%) condition: 48.6/60.0 Wh (81.0%)
volts: 16.6 min: 15.2 model: SMP DELL JJPFK87 type: Li-poly serial: <filter>
status: full
CPU:
Info: model: Intel Core i7-9750H bits: 64 type: MT MCP arch: Coffee Lake
gen: core 9 level: v3 note: check built: 2018 process: Intel 14nm family: 6
model-id: 0x9E (158) stepping: 0xA (10) microcode: 0xF0
Topology: cpus: 1x cores: 6 tpc: 2 threads: 12 smt: enabled cache:
L1: 384 KiB desc: d-6x32 KiB; i-6x32 KiB L2: 1.5 MiB desc: 6x256 KiB
L3: 12 MiB desc: 1x12 MiB
Speed (MHz): avg: 1849 high: 2600 min/max: 800/4500 scaling:
driver: intel_pstate governor: powersave cores: 1: 2600 2: 800 3: 800
4: 2600 5: 2600 6: 2600 7: 799 8: 2600 9: 800 10: 2600 11: 2600 12: 800
bogomips: 62399
Flags: avx avx2 ht lm nx pae sse sse2 sse3 sse4_1 sse4_2 ssse3 vmx
Vulnerabilities: <filter>
Graphics:
Device-1: Intel CoffeeLake-H GT2 [UHD Graphics 630] vendor: Dell
driver: i915 v: kernel arch: Gen-9.5 process: Intel 14nm built: 2016-20
ports: active: none off: eDP-1 empty: DP-1, DP-2, HDMI-A-1, HDMI-A-2
bus-ID: 00:02.0 chip-ID: 8086:3e9b class-ID: 0300
Device-2: NVIDIA TU106M [GeForce RTX 2060 Mobile] vendor: Dell
driver: nvidia v: 530.41.03 alternate: nouveau,nvidia_drm non-free: 530.xx+
status: current (as of 2023-03) arch: Turing code: TUxxx
process: TSMC 12nm FF built: 2018-22 pcie: gen: 1 speed: 2.5 GT/s lanes: 8
link-max: gen: 3 speed: 8 GT/s lanes: 16 bus-ID: 01:00.0
chip-ID: 10de:1f11 class-ID: 0300
Device-3: Microdia Integrated_Webcam_HD type: USB driver: uvcvideo
bus-ID: 1-5:4 chip-ID: 0c45:671f class-ID: 0e02
Display: x11 server: X.Org v: 21.1.8 with: Xwayland v: 23.1.1
compositor: kwin_x11 driver: X: loaded: modesetting,nvidia unloaded: nouveau
alternate: fbdev,intel,nv,vesa dri: iris gpu: i915 display-ID: :0
screens: 1
Screen-1: 0 s-res: 2560x2160 s-dpi: 96 s-size: 675x570mm (26.57x22.44")
s-diag: 883mm (34.78")
Monitor-1: DP-1-0 pos: primary,top res: 2560x1080 hz: 60 dpi: 81
size: 798x334mm (31.42x13.15") diag: 865mm (34.06") modes: N/A
Monitor-2: HDMI-1-0 pos: bottom res: 2560x1080 hz: 60 dpi: 96
size: 677x290mm (26.65x11.42") diag: 736mm (29") modes: N/A
Monitor-3: eDP-1 size-res: N/A modes: N/A
API: OpenGL v: 4.6 Mesa 23.0.1 renderer: Mesa Intel UHD Graphics 630 (CFL
GT2) direct-render: Yes
Audio:
Device-1: Intel Cannon Lake PCH cAVS vendor: Dell driver: snd_hda_intel
bus-ID: 1-4.1:5 v: kernel chip-ID: 1b3f:2008
alternate: snd_soc_skl,snd_sof_pci_intel_cnl bus-ID: 00:1f.3
class-ID: 0300 chip-ID: 8086:a348 class-ID: 0403
Device-2: NVIDIA TU106 High Definition Audio vendor: Dell
driver: snd_hda_intel v: kernel pcie: gen: 3 speed: 8 GT/s lanes: 8
link-max: lanes: 16 bus-ID: 01:00.1 chip-ID: 10de:10f9 class-ID: 0403
Device-3: Generalplus USB Audio Device type: USB
driver: hid-generic,snd-usb-audio,usbhid
Device-4: Realtek USB Audio type: USB driver: snd-usb-audio
bus-ID: 1-4.5:9 chip-ID: 0bda:4014 class-ID: 0102 serial: <filter>
API: ALSA v: k6.2.9-zen1-1-zen status: kernel-api with: aoss
type: oss-emulator tools: N/A
Server-1: PipeWire v: 0.3.67 status: active with: 1: pipewire-pulse
status: active 2: wireplumber status: active 3: pipewire-alsa type: plugin
4: pw-jack type: plugin tools: pactl,pw-cat,pw-cli,wpctl
Network:
Device-1: Realtek vendor: Dell driver: r8169 v: kernel pcie: gen: 1
speed: 2.5 GT/s lanes: 1 port: 3000 bus-ID: 3c:00.0 chip-ID: 10ec:2502
class-ID: 0200
IF: enp60s0 state: down mac: <filter>
Device-2: Qualcomm Atheros QCA6174 802.11ac Wireless Network Adapter
vendor: Dell driver: ath10k_pci v: kernel pcie: gen: 1 speed: 2.5 GT/s
lanes: 1 bus-ID: 3d:00.0 chip-ID: 168c:003e class-ID: 0280 temp: 48.0 C
IF: wlp61s0 state: down mac: <filter>
Device-3: Realtek RTL8153 Gigabit Ethernet Adapter type: USB driver: r8152
bus-ID: 6-1.2:3 chip-ID: 0bda:8153 class-ID: 0000 serial: <filter>
IF: enp58s0u1u2 state: up speed: 1000 Mbps duplex: full mac: <filter>
Bluetooth:
Device-1: Qualcomm Atheros type: USB driver: btusb v: 0.8 bus-ID: 1-14:8
chip-ID: 0cf3:e007 class-ID: e001
Report: bt-adapter ID: hci0 rfk-id: 0 state: up address: <filter>
Drives:
Local Storage: total: 1.14 TiB used: 538.63 GiB (46.0%)
SMART Message: Unable to run smartctl. Root privileges required.
ID-1: /dev/nvme0n1 maj-min: 259:0 vendor: Western Digital
model: PC SN520 NVMe WDC 256GB size: 238.47 GiB block-size: physical: 512 B
logical: 512 B speed: 15.8 Gb/s lanes: 2 type: SSD serial: <filter>
rev: 20240012 temp: 51.9 C scheme: GPT
ID-2: /dev/sda maj-min: 8:0 vendor: Western Digital
model: WD10SPZX-75Z10T3 size: 931.51 GiB block-size: physical: 4096 B
logical: 512 B speed: 6.0 Gb/s type: HDD rpm: 5400 serial: <filter>
rev: 4514 scheme: GPT
Partition:
ID-1: / raw-size: 221.19 GiB size: 221.19 GiB (100.00%)
used: 63.78 GiB (28.8%) fs: btrfs dev: /dev/nvme0n1p2 maj-min: 259:2
ID-2: /boot/efi raw-size: 300 MiB size: 299.4 MiB (99.80%)
used: 624 KiB (0.2%) fs: vfat dev: /dev/nvme0n1p1 maj-min: 259:1
ID-3: /home raw-size: 221.19 GiB size: 221.19 GiB (100.00%)
used: 63.78 GiB (28.8%) fs: btrfs dev: /dev/nvme0n1p2 maj-min: 259:2
ID-4: /var/log raw-size: 221.19 GiB size: 221.19 GiB (100.00%)
used: 63.78 GiB (28.8%) fs: btrfs dev: /dev/nvme0n1p2 maj-min: 259:2
ID-5: /var/tmp raw-size: 221.19 GiB size: 221.19 GiB (100.00%)
used: 63.78 GiB (28.8%) fs: btrfs dev: /dev/nvme0n1p2 maj-min: 259:2
Swap:
Kernel: swappiness: 133 (default 60) cache-pressure: 100 (default)
ID-1: swap-1 type: zram size: 15.43 GiB used: 0 KiB (0.0%) priority: 100
dev: /dev/zram0
ID-2: swap-2 type: partition size: 16.98 GiB used: 0 KiB (0.0%)
priority: -2 dev: /dev/nvme0n1p3 maj-min: 259:3
Sensors:
System Temperatures: cpu: 69.0 C pch: 69.0 C mobo: 65.0 C
Fan Speeds (RPM): cpu: 2418 fan-1: 2353
Info:
Processes: 323 Uptime: 1h 12m wakeups: 3 Memory: 15.43 GiB
used: 6.72 GiB (43.5%) Init: systemd v: 253 default: graphical
tool: systemctl Compilers: gcc: 12.2.1 Packages: pm: pacman pkgs: 1920
libs: 531 tools: gnome-software,octopi,pamac,paru,yay pm: appimage pkgs: 0
Shell: Zsh v: 5.9 running-in: kitty inxi: 3.3.26
Garuda (2.6.16-1):
System install date: 2023-04-01
Last full system update: 2023-04-06
Is partially upgraded: No
Relevant software: snapper NetworkManager dracut nvidia-dkms
Windows dual boot: No/Undetected
Failed units: