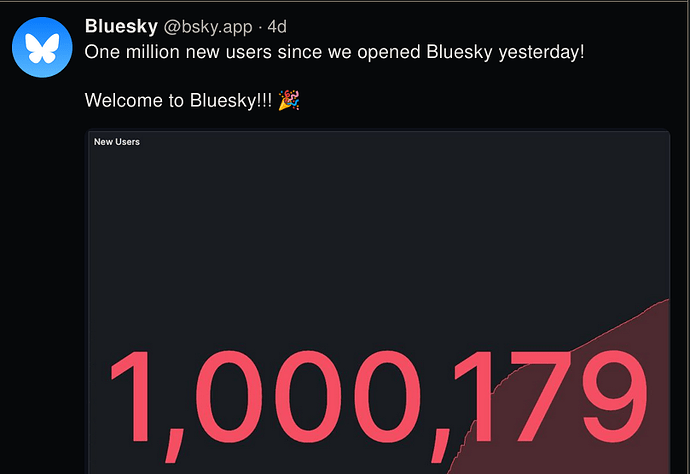
and doesn’t let you sign up… Rate Limit Exceeded message
Now it works without invitation, probably the servers are overloaded.
Nginx has been forked, and seems to be taking at least half of the development power along with it. Seems to be at least partly related to a disagreement about CVE assignment.
Petr Tesarik with Huawei sent out the “request for comments” patch series on the new SandBox Mode. Petr describes the SandBox Mode as:
"The ultimate goal of SandBox Mode is to execute native kernel code in an environment which permits memory access only to predefined addresses, so potential vulnerabilities cannot be exploited or will have no impact on the rest of the kernel.
This patch series adds the API and arch-independent infrastructure of SandBox Mode to the kernel. It runs the target function on a vmalloc()'ed copy of all input and output data. This alone prevents some out-of-bounds accesses thanks to guard pages."
CVE-2023-52160 is now public as the WPA_Supplicant vulnerability that can allow an attacker to trick a victim into connecting to a malicious clone of an enterprise WiFi network and in turn intercepting all traffic. This affects both Android, Chrome OS, and Linux systems relying on WPA_Supplicant.
A single packet can exhaust the processing capacity of a vulnerable DNS server, effectively disabling the machine, by exploiting a 20-plus-year-old design flaw in the DNSSEC specification.
That would make it trivial to take down a DNSSEC-validating DNS resolver that has yet to be patched, upsetting all the clients relying on that service and make it seem as though websites and apps were offline.
The academics who found this flaw – associated with the German National Research Center for Applied Cybersecurity (ATHENE) in Darmstadt – claimed DNS server software makers briefed about the vulnerability described it as “the worst attack on DNS ever discovered.”
For software relying heavily on indirect draws will see a “massive boost” in performance.
The chip, called Earl Gray, uses a RISC-V-based processor core and includes a number of built-in security and cryptography hardware modules. The project was started in 2019 by a coalition of companies founded by Google and led by lowRISC, a non-profit organization in Cambridge, UK. Modeled after open source software projects, it is developed by contributors from around the world, both official project partners and independent engineers.
OpenTitan uses a hardware-based Root-of-trust (RoT) security protocol. The idea is to provide an on-chip source of cryptographic keys that is not accessible remotely. Since the key is otherwise inaccessible, the system can be confident that it has not been tampered with, providing a basis for security. Regular proprietary chips can also use RoT technology. Proponents say open access provides an additional layer of trust. Since anyone can test and examine the design, it is theoretically more likely that errors will be noticed and their corrections can be verified.
Rizzo and Ferris believe their chip provides a template for open-source hardware development that other teams will copy.
Once the methodology is proven, others will pick it up, says Rizzo. — If you look at what happened with open source software, at first people thought it was some kind of attempt to break free, and then it turned out that it works on almost every mobile phone. It simply seized power because it has certain valuable properties. And I think we’re now seeing the beginning of this in silicon.
RISC-V ISA is a concept and not a thing. The RISC-V Foundation does not sell processors or licenses. China’s interest in RISC-V suggests it is more about building a future that is not beholden to the whims of others. For this very reason, RISC-V will grow everywhere — including China.
Even if valid security concerns about RISC-V were identified, behemoth companies like Intel, Google and Siemens would do everything in their power to ensure the architecture remained spy-proof and free of back doors. Such measures could include guard rails to prevent RISC-V from being used for military applications.
A US exit from the RISC-V market would play directly into China’s hands. It would grant Beijing exactly what it wanted: unrestricted access to a leading-edge chip technology with no American strings attached.
Moreover, America’s voluntary abdication of RISC-V stakeholder status would reduce the country’s global influence. US allies would be forced to make an uncomfortable choice about whether to abandon a budding but promising technology. Their decisions might well disappoint American China hawks.
Biden’s recent chip sanctions have had limited success in hindering China and enhancing American security. A decision to pull out of RISC-V would not only fail by those metrics; it would strengthen America’s biggest rival. The operative word again is backfire.
IP collaborations helped propel RISC-V-based innovation in Europe last year, targeting processing speeds that meet the growing performance requirements of artificial intelligence and machine learning applications. The ability of RISC-V to coalesce multiple components within a single chip or SoC will be a key growth driver this year and beyond, but what will perhaps be most interesting to watch is how effectively the architecture can penetrate new and diverse application sectors.
Collaborative activity in Europe last year underscored this trend. For example, Semidynamics partnered with Signature IP to produce a fully tested RISC-V, multicore environment and coherent hub interface (CHI) interconnect for the development of state-of-the-art chip designs. Semidynamics’ new RISC-V Tensor Unit (Figure 2) combines the company’s core vector unit and an array unit, eliminating the need to purchase separate NPUs, GPUs or additional components.
The recent advances are also raising RISC-V’s profile in the automotive industry, which is turning to the open ISA to enhance the capabilities of automated driving systems and is exploring the prospects for using RISC-V to help lower the power consumption and cost of EVs. An uptick in RISC-V-based automotive collaborations this year would signal that RISC-V will need to keep pace with technological developments in electric and autonomous vehicles.
Reducing supply chain reliance, which indicates a potential benefit in terms of autonomy and control over key components, might just be the next differentiating step for IP companies in the competitive automotive market.
A challenge for RISC-V companies in the automotive market is addressing the security goals toward which the entire community is working. The base RISC-V ISA does not specify a comprehensive set of security features. Security mechanisms such as hardware-enforced memory protection, virtualization support and other advanced security features are often left to be implemented by individual designers.
Standardization would go a long way toward providing the needed consistency in security approaches, and IP companies, recognizing the need, have been introducing standard security protocols in their product portfolios.
Investment in the RISE project by high-profile members such as Google and Qualcomm could accelerate innovation in the RISC-V ecosystem. But how soon the RISC-V software objectives can be met remains an open question.
…continuing to further enhance the performance of this open-source AV1 decoder on x86_64 Intel/AMD processors too.
![]()
Proton Mail was my primary mailing service…
Ouch… governments are bit by bit getting rid of anonymous services, eh?
Luckily, there are still some solid options out there (mailbox.org, posteo.de, etc), but I know from experience that it can be quite a struggle to swit h email adresses.
I hope they don’t ban proton VPN ![]()
They’d never know if a good VPN was ever there, right? ![]()
AFAIK, If a VPN operates in India then they needs to keep logs of the users , if user is found to have committed or involved in a crime so the cyber police can ask for logs and the VPN company will have to give it to them .
I can be wrong either, most of the time government gets much more pleasure in banning Chinese sites and apps, now they are slowly doing some of things with Chinese hardwares too,
for which I don’t have any complain .
But proton VPN can also get banned …maybe … ![]()
Probably they won’t ban mobile apps…
Using a different dns provider should surpass the issue.
Else I can always use a VPN.
As far as I know proton mails are already banned in a few countries and some websites actively block you from signing up on them with proton mail. The “country issue” is why proton vpn was actually even made.
“In 2022, NordVPN closed its physical servers in India in response to the CERT-In’s order for VPN companies to store consumers’ personal data for a period of five years.” ~Wikipedia.
I’m glad I don’t live in…nevermind, everybody would rather live some place different. I would rather live in Germany, for instance. ![]()
EDIT: I would add that, just because a company closes its physical servers in a specific country, it does not preclude citizens from accessing a server located remotely (outside that country). Unless it is illegal for citizens to do so. ![]()